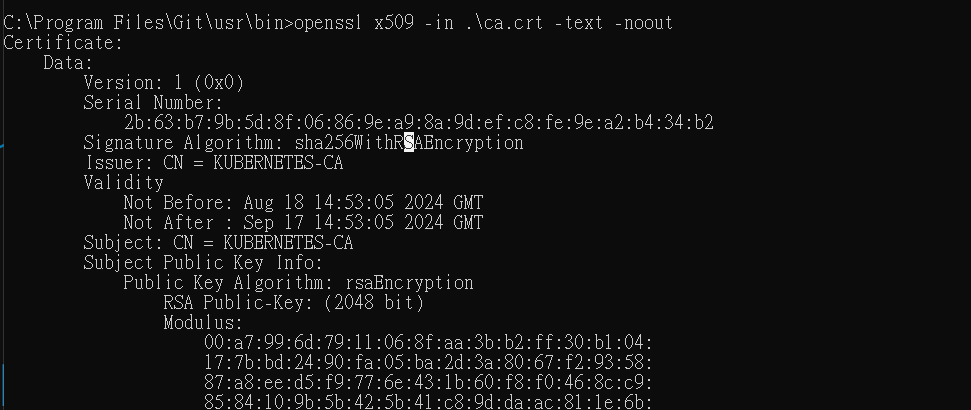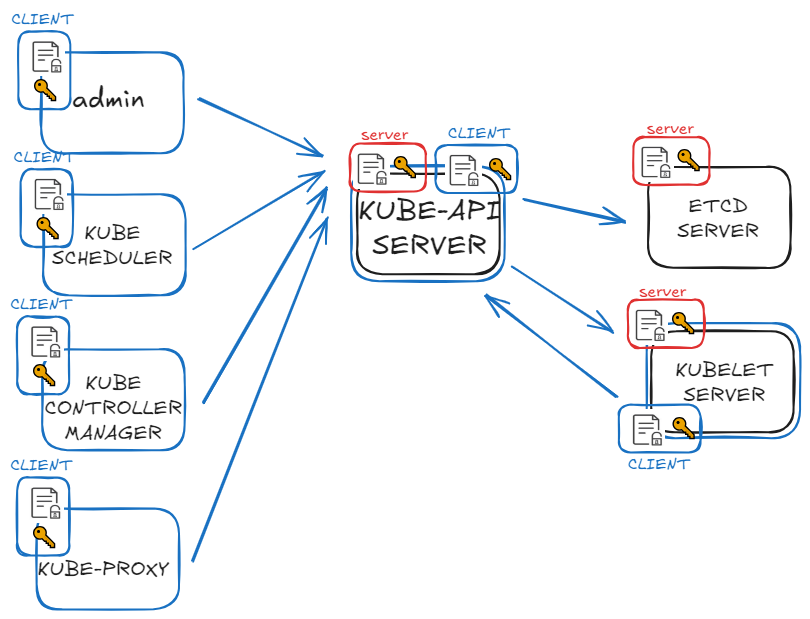
在上一篇提到,建立K8s叢集內管理員及元件的憑證,在後續若有新的使用者加入,需處理的流程:
由於CA server及其擁有的憑證,具有建立任何權限角色的能力,只會放在特定安全的server(the one and only),每次要簽署憑證都需登入該server,使用規模擴大時,這些過程變得繁瑣
K8s提供憑證API,流程改變如下:
CertificateSigningRequest
CertificateSigningRequest 傳送至CA server (如:control plane)kubectl get csr
kubectl certificate approve <xxx>
kubectl certificate deny <xxx>
舉例:Doe為叢集新使用者
openssl genrsa -out doe.key 2048
openssl req -new -key doe.key -subj "/CN=doe" -out doe.csr
cat doe.csr | base64
apiVersion: certificates.k8s.io/v1beta1
kind: CertificateSigningRequest
metadata:
name: doe
spec:
groups:
- system:authenticated
usages:
- digital signature
- key encipherment
- server auth
# 編碼後的內容放在request
request:
<base64編碼後的CSR>
建立憑證後,使用者可存取叢集,下一個關卡:限定使用者可存取的環境
kubectl所用的憑證,統一置於kubeconfig file,預設會去查 $HOME/.kube/config,包含有3部份:
apiVersion: v1
kind: Config
# 初始的上下文 使用者 @ cluster
current-context: admin@my-kube-playground
clusters:
- name: my-kube-playground
certificate-authority: etc/kubernetes/pki/ca.crt
certificate-authority-data: 或用此欄位,放入 base64編碼的ca file
server: https://172.17.0.5:6443
- name: development
certificate-authority-data:
server:
contexts:
- name: admin@my-kube-playground
context:
cluster: my-kube-playground
user: admin
# 綁定namespace
namespace: test-namespace
users:
- name: admin
client-certificate: etc/kubernetes/pki/users/admin.crt
client-key: etc/kubernetes/pki/users/admin.key
config指令
# 查看預設config
kubectl config view
# 查看特定config
kubectl config view –kubeconfig=my-custom-config
# 使用特定的context
kubectl config use-context admin@my-kube-playground
#查看說明
kubectl config -h
平時從瀏覽器可以直接點選查看憑證內容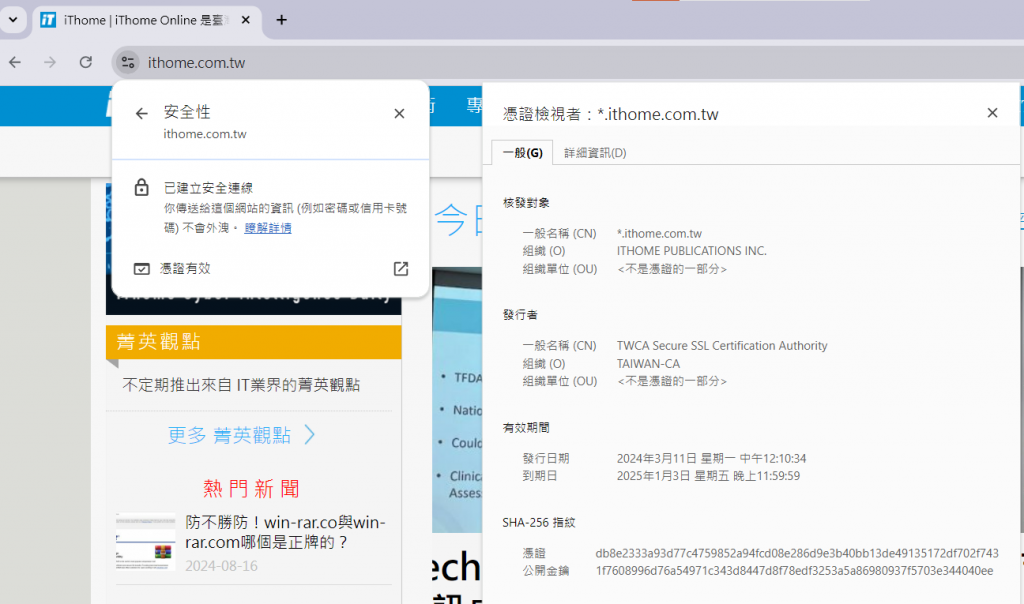
ps -aux | grep kubelet
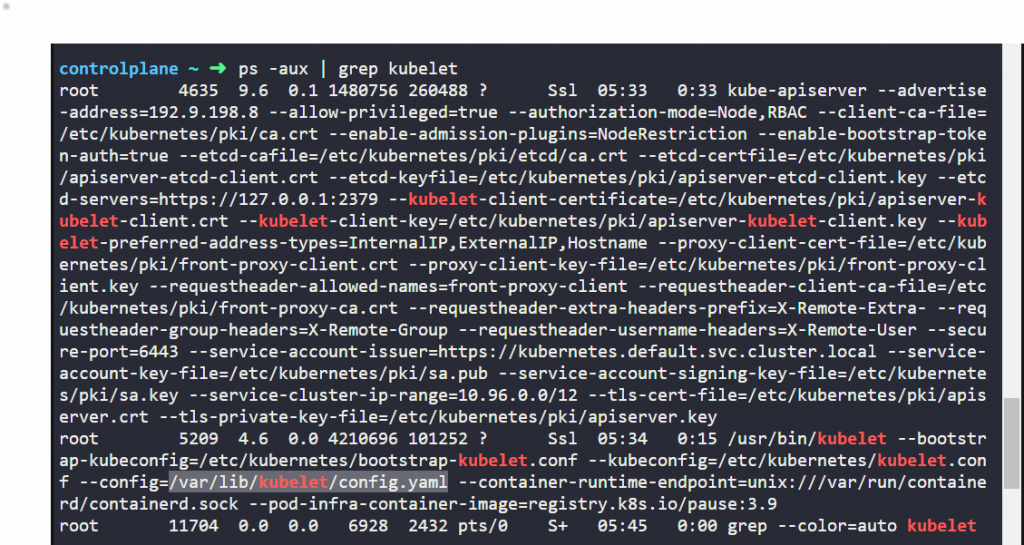
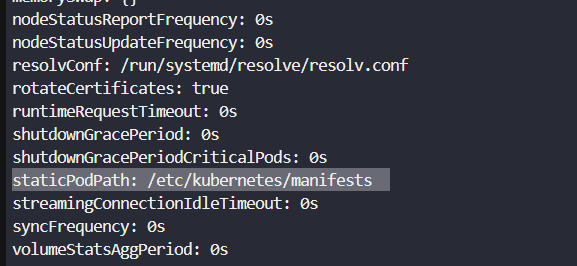
cat /var/lib/kubelet/config.yaml
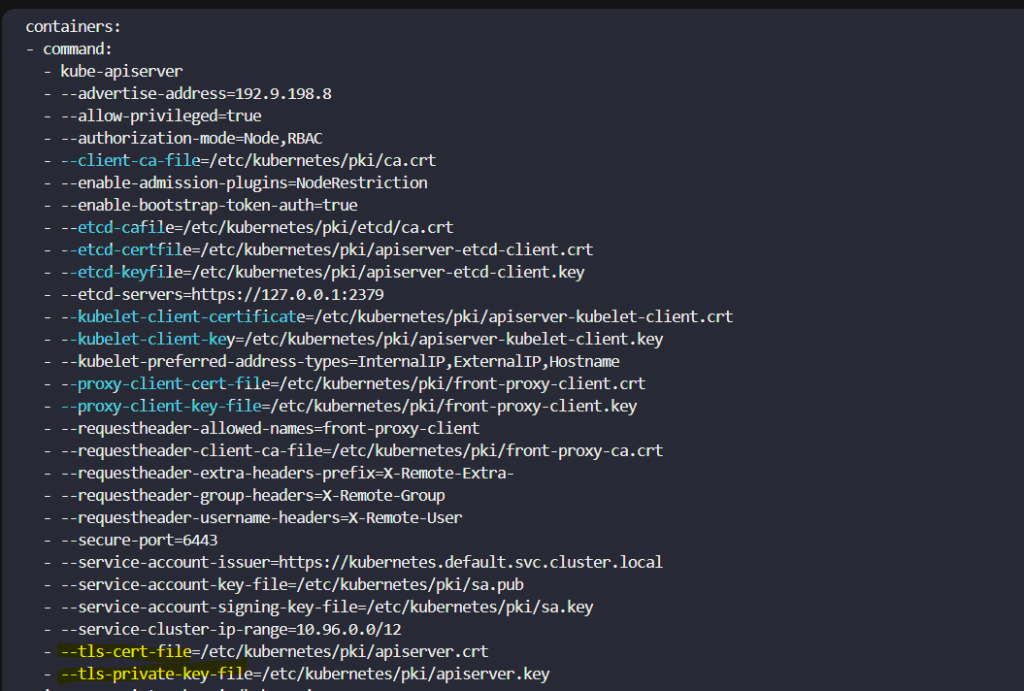
cat /etc/kubernetes/manifests/kube-apiserver.yaml
openssl x509 -in /etc/kubernetes/pki/apiserver.crt -text -noout